Introduction to encryption
In the online world encryption disguises data rearranging the data bits so that nobody can read or see the information without the secret key, this key can consist of a password or a digital file, aka keyfile, encryption secures plain text as well as any other digital media like photos, videos or software, you can also encrypt a whole operating system and a partition.
To secure data, encryption uses mathematic functions known as cryptography algorithms, aka ciphers, some example of well known and trusted cryptography algorithms are AES, Blowfish, Twofish and Serpent, these ciphers can be subcategorized with a number indicating its strength in bits.
An encryption algorithm key length indicates its size measured in bits, the length indicating the algorithm strentgh in bits will always be even (bit is binary unit composed of zeros and ones), these keys are used to control the operation of a cipher.
The more mathematical strength the encryption algorithm has the more difficult it will be to crack it without access to the key but a strong cipher normally requires more computational power, a few seconds of wait might not matter much to the home user but for businesses dealing with thousands of calculations each hour to decrypt/encrypt data in their servers it will mean that more money has to be spent in hardware and electricity.
Why not all websites use encrypted SSL connections
If all of the websites on the Internet used encrypted SSL connections the servers serving content using SSL (Secure Socker Layer) would need more CPU power and more electricity, when you multiply this by millions of pages served each second, costs dramatically add up, page loading would also be slower because the decryption process needs to take place in the computer and those using very low end processors in mobile devices would suffer speed the most.
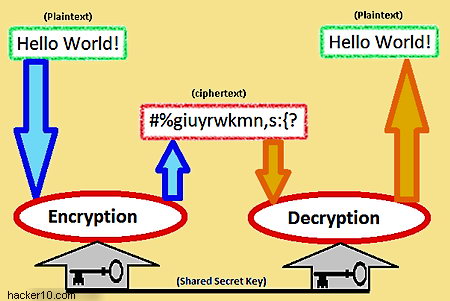
Symmetric encryption diagram
When choosing an encryption algorithm it is important to look at is many factors, not only key size, when it comes to security how an algorithm has been implemented is much more important than key length, algorithm perfomance also matters, if people had to wait an hour to encrypt and decrypt files encryption would become unusable, a trade off in between security and usability needs to be established, the best is to always choose a standard algorithm that has been widely scrutinised by experts, aka cryptographers.
What encryption key length should I choose?
An AES 128-bit encryption key is considered very strong and suitable to withstand future attaks, the U.S. Government requires 192 or 256-bit AES encryption keys for highly sensitive data, AES is the standard US Government encryption algorithm for data encryption.
A 128-bit key, can have more than 300,000,000,000,000,000,000,000,000,000,000,000 key combinations.
The importance of choosing a strong password for encryption
Encryption software gathers random data before encrypting your files, aka entropy, the password you use will be part of this random data gathered to cipher the files, hence why it is very important that you choose a long passphrase, in addition, you should not use any dictionary words to thwart brute force attacks.
A brute force attack consists of an automatic process where all of the dictionary words are quickly whirled at the password login prompt, as computers have become increasingly faster this can be done in a matter of hours or less using cloud computing.
Encryption security tips
- Always choose an encryption program that uses a standard cipher that has been scrutinised by experts, e.g AES
- Do not use dictionary words as your password, use a long passphrase made up of capital and small letters with punctuation signs and numbers
- Do not use the passphrase you use to encrypt your data for anything else like your webmail password or an online forum which security can be compromised
- Never trust a third party service to store your encryption keys or carry out the encryption implementation, if you store data online encrypt it yourself in your computer
- Watch out for keyloggers and malware in your computer that could capture your keystrokes and your secret passphrase, use an updated antivirus and firewall
- Never reveal to anyone your password, not even to a support department whose staff could be outsourced in a crime ridden country or could be impersonating someone else
Encryption links for beginners
National Cryptologic Museum Foundation
Intypedia Information Security
Bruce Schneier’s blog (Cryptographer)
Tq http://www.hacker10.com
No comments:
Post a Comment